The real-world effects of cyber liability on industry

There is a common misconception that the effects of cyber attacks are limited to the digital world. A phishing attack leads to a data breach. A ransomware attack results in encrypted files. A denial of service (DNS) attack on a website results in the site being offline. All costly. All inconvenient. But all effectively limited to a virtual space.
The truth is much more complicated. In today’s ever-more-connected world, a hacker from hundreds or even thousands of miles away can cause IRL (In Real Life) consequences like fires, explosions and even chemical spills. That’s right. Cyber crime or cyber terrorism can be a pollution liability risk.
Imagine this. You work for a water treatment authority that is interviewing for a new IT staffer. One of the rejected applicants takes the decision personally and decides to retaliate by hacking your systems. Once compromised, the attacker is able to release hundreds of thousands of liters of raw sewage, resulting in extensive environmental and physical damage.
If you think that sounds like a plotline from a new streaming crime drama, you’d be wrong. That very scenario happened in Australia back in 2000. You might be tempted to further think, “That was SO long ago. Systems are much more secure now.”
Again, you’d be wrong.
Of course, there are more sophisticated tools available to protect against attacks. But there are also much more sophisticated techniques that cyber attackers are using. There is a literal arms race going on in this global digital ecosystem with the good guys trying to stay a step ahead of the bad guys. And vice versa.
What’s in a name?
Terms such as cyber-crime and cyber terrorism seem to be interchangeable and somewhat confusing.
- Cyber-crime is generally defined as a crime in which a computer is the target (hacking, phishing, spamming, etc.) or is used as a tool to commit an offense
- Cyber terrorism uses the internet to conduct violent acts that result in, or threaten, loss of life or significant bodily harm, in order to achieve political or ideological gains through threat or intimidation
Strip away the term “cyber” and definitions are analogous to their IRL cousins. A key difference is that the weapon of choice is lines of code.
Are you a target?
No organization is immune to cyber threats. But as with all risks, the effects greatly vary by industry. Of the critical industries and infrastructure identified by the US Department of Homeland Security (DHS), there are numerous categories that have pollution exposures from a cyber-attack, including:
- Refineries
- Bulk storage facilities
- Pipelines
- Power plants
- Wastewater treatment plants
There’s a cliché for that
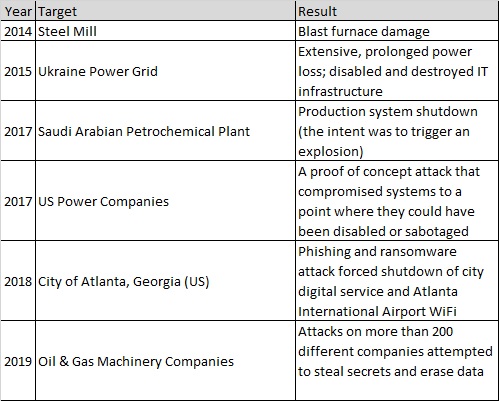
It’s said that those who do not learn from history are doomed to repeat it. That is certainly true in the realm of cyber risk. Here are a few notable examples of cyber-attacks from the last few years:
Being vulnerable. And not in a good way
Companies are at risk of attacks that come in two basic categories – opportunistic and targeted. Most attacks via the internet fall into the former category.
As the name implies, attacks take place when a vulnerability is found. Targeted attacks, on the other hand, are aimed at a specific person or entity for a specific reason. Because targeted attacks are tailored to the intended victim, they are harder to combat.
In either case, hackers will deploy a variety of tactics to penetrate a network and organizations must pay attention to threats that can come from:
- Malware
- Unsecured wireless connections
- Social engineering, such as phishing
- USB devices
- Unsecured network connections
- Poor data storage/data security practices
- Substandard physical security
What a tangled web
The “Internet of Things” (IOT) has created a world of connected convenience. It has also help create a world of increased cyber liability. We’ve heard stories of residential camera and other home systems being hacked. And just like homes use IOT and other interconnected systems for convenience and efficiency, so do critical industries used for petroleum, chemical, manufacturing, marine, water/wastewater and electric utility facilities.
These highly complex systems control operations that have the capacity to release poisonous chemicals, crude oil, toxic gases and even sewage. The transportation industry also relies on these systems to get people and materials safely from place to place. Vulnerabilities in these systems can result in devastating consequences.
New innovations bring new risks
The very nature of what makes tech so beneficial is also what makes it so risky. Every new tech advance brings with it a commensurate set of risks. Areas of emerging risk include:
- 5G technology
- Cloud services
- Autonomous vehicles and drones
- Artificial intelligence (AI) and machine learning
- “Internet of Things”
Even a relatively benign system, like traffic navigation, can be vulnerable in ways its developers never imagined. For example, in February 2020, a German artist turned Google Maps against itself using nothing but a wagonload of 99 mobile devices using Google Maps. As he walked slowly through the streets with the wagon, the result was a traffic jam that didn’t even exist. Even though his intention was ostensibly artistic expression, the result was a well-established system that was disrupted in a completely new way. Just imagine the damage that hacked transportation safety systems could create from accidents involving multiple hazardous materials.
But there’s good news
It may sound like fighting the hackers is an uphill battle. And sometimes it is. But there are steps your organization can take to protect itself, especially the following:
- Appointing a cyber security officer
- Managing access control to company computer systems
- Implementing effective password management
- Setting appropriate levels of system access for each user
- Providing effective and recurring training and awareness
- Implementing system monitoring and incident management
- And more
Yes. It can happen to you. And probably will
You don’t need to be a major multinational corporation to be victim of a cyber attack. Remember, one of the largest data breaches happened because a relatively small HVAC contractor had access to Target’s systems that were vulnerable to attack.
And, unfortunately, there is no cookbook or “off the shelf” prevention template with blanks to be filled in for critical industry cyber security. You must perform in-depth vulnerability analysis of your operations, equipment, procedures, physical security and personnel to develop a security program tailored to deter and manage cyber exposures.
Authored by AXA XL
If you would like to talk to AXA XL about the issues raised in this article, CLICK HERE, leave a message and youTalk-insurance will pass your enquiry on
About AXA XL
AXA XL is the P&C and specialty risk division of AXA which provides property, casualty, professional and speciality products to industrial, commercial and professional firms, insurance companies and other enterprises, here in the UK and throughout the world. With underwriting teams based in the US, UK, EMEA and Asia Pacific regions, we can make decisions close to the markets you serve and work with you to tailor cover to your business needs.
We help businesses adapt and thrive amidst change. Rather than just paying covered claims when things go wrong, we go beyond protection into prevention so your business can go beyond the unexpected.

